TruffleNet in AWS: How Stolen Credentials Turn Into Cloud-Scale Fraud, and How to Stop It
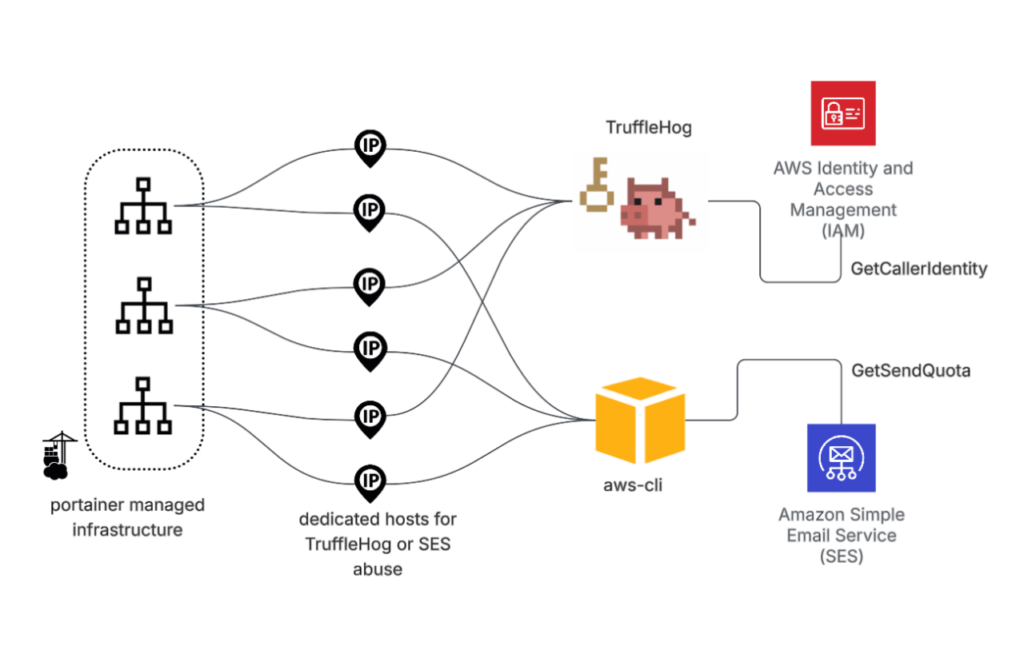
Introduction If you use AWS, remember that attackers frequently do not break in by hacking software. Instead, they usually log in with valid credentials. TruffleNet shows this clearly. Rather than using a single exploit, it works by using stolen AWS keys to test whether they work, then abusing cloud services, especially email, to make money […]
SOC 2 for AI Startups: Applying Trust Services Criteria to AI Products

The use of Artificial Intelligence, or AI, has been drastic and quick. The development of new products by AI startups is one of the major causes of this. Such products are capable of learning, thinking, and doing several other things for people. Acceptance of AI products by the public at large will not be possible without trust being built […]
How Long SOC 2 Really Takes: A Practical Timeline for 2026

SOC 2 timelines are often presented as predictable. Three months. Six months. Sometimes the timeline is shorter if the tooling is appropriate. In practice, that framing rarely holds up, especially for startups and small teams operating under constant change. By 2026, SOC 2 has settled into something closer to an operational maturity signal than a one-time compliance exercise. The framework itself hasn’t changed much. What […]
AI-Driven Threat Modeling: How Modern Teams Predict Attacks Before They Happen
Cyberattacks are becoming more frequent and damaging in today’s digital space. Conventionally, security defenses completely depend on post incident responses that are not at all sufficient. Modern security teams are choosing AI threat modeling services as a proactive approach to predict, mitigate risks, and anticipate before they even materialize. By combining human insight with artificial […]
The Human Hacker’s New Toolkit: Why AI Is Our Best Drone in 2025
Let’s cut the corporate jargon. In offensive security, 2025 isn’t about if AI changes vulnerability assessment and penetration testing [VAPT]; it’s about acknowledging that the threat landscape is now running at machine speed. If you’re still selling a static, three-week pen test, you’re selling a false sense of security that the adversary will exploit in […]
The Most Common SOC 2 Gaps Found in Startup Security Assessments

Most startups don’t fail SOC 2 because they ignore security. They fail because what they believe is “covered” isn’t operating the way they think it is. On paper, things look reasonable. Policies exist. Tools are in place. Access seems controlled. Then a security assessment starts. That’s usually when assumptions get exposed. A soc 2 gap assessment doesn’t uncover dramatic breaches. It reveals quiet mismatches between intention […]
SOC 2 Compliance in 2026: What Startups & SMEs Need to Know

SOC 2 has never been just a certification exercise. By 2026, that reality becomes harder to ignore. For startups and small- to mid-sized businesses, compliance is no longer treated as a future checkbox. It’s increasingly viewed as a signal of operational maturity. What’s changing isn’t the framework itself, but how it’s interpreted. Auditors, customers, and partners are paying closer attention to how controls function, […]
A Practical Guide on Prompt Injection – Part 1

What is Prompt Injection? Prompt Injection is a type of attack where an adversary manipulates the input (prompt) given to a large language model (LLM) in order to override its original instructions or security controls. In simple terms, the attacker tricks the AI into: This happens because LLMs prioritize user input commands over system-level instructions […]
Rate-Limit Bypass by Adding a Space: Simple Yet Abusable

Every application attempts to protect the Forgot Password feature from abuse. After all, nobody wants their inbox flooded with endless reset emails. Rate limiting is supposed to prevent exactly that. But sometimes, even solid security controls fail for the simplest reasons. This vulnerability is one of those “wait… seriously? 🤨” moments where adding just a […]
React2Shell: A Critical Vulnerability in Modern Frontend Frameworks
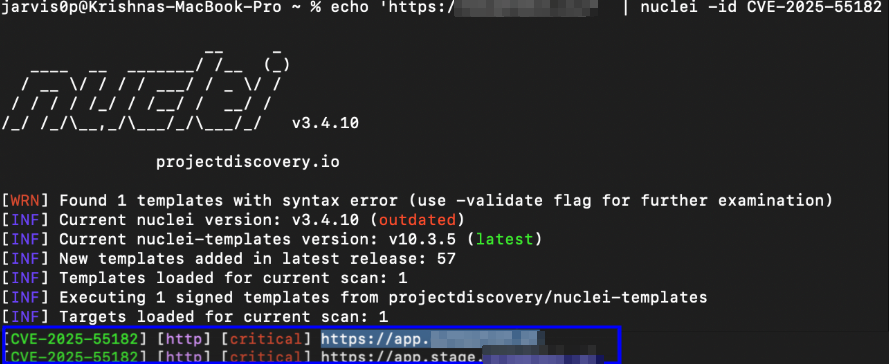
What is React2Shell (CVE-2025-55182)? A critical vulnerability with CVSS of 10.0 called React2Shell has been discovered in React’s Flight protocol that could allow attackers to execute arbitrary code on servers running React Server Components. CVE-2025-55182 affects multiple popular frameworks, including Next.js, React Router, React Server Components, and Waku, with exploitation possible under default configurations. Upon […]

