AI-Driven Threat Modeling: Predicting Attacks Before They Happen

Cyberattacks are becoming more frequent and damaging in today’s digital space. Conventionally, security defenses completely depend on post incident responses that are not at all sufficient. Modern security teams are choosing AI threat modeling services as a proactive approach to predict, mitigate risks, and anticipate before they even materialize. By combining human insight with artificial […]
The Backdoor in the Cloud: Risks of Overly Permissive Azure SAS
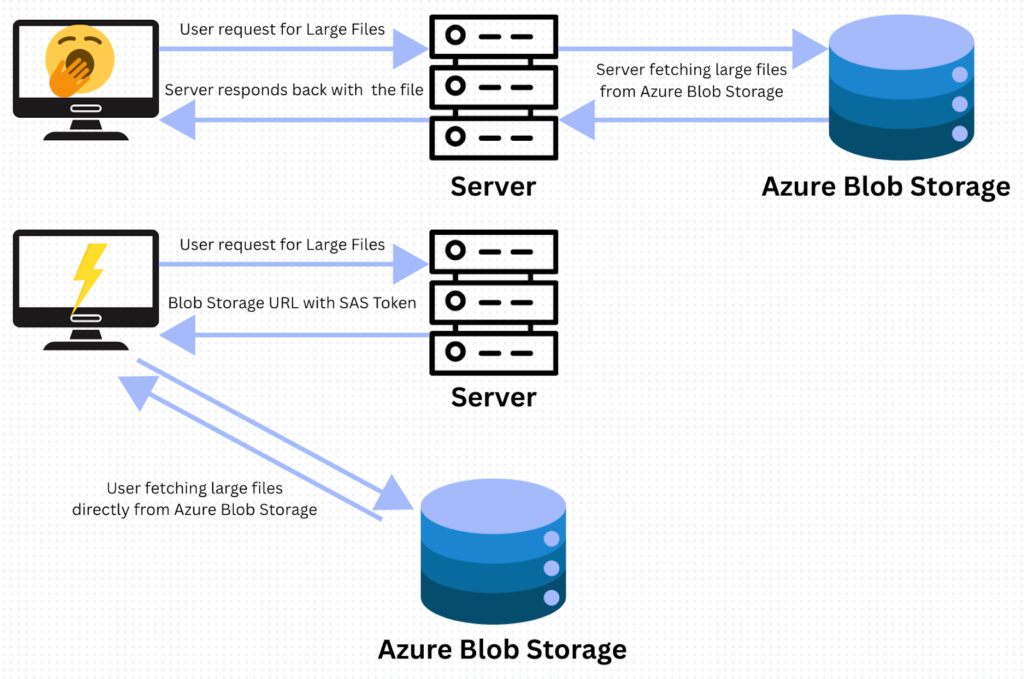
I. Executive Summary: The Quiet Catastrophe of Token Mismanagement Modern digital operations depend on massive data stores. Transactional data often sits in structured databases, while large volumes of unstructured content such as media, JavaScript assets, logs, and backups are kept in cloud object storage. Azure Blob Storage is a core service built for availability, scale […]
Beginners Recon Workflow for Bug Bounty & Web Pentesting
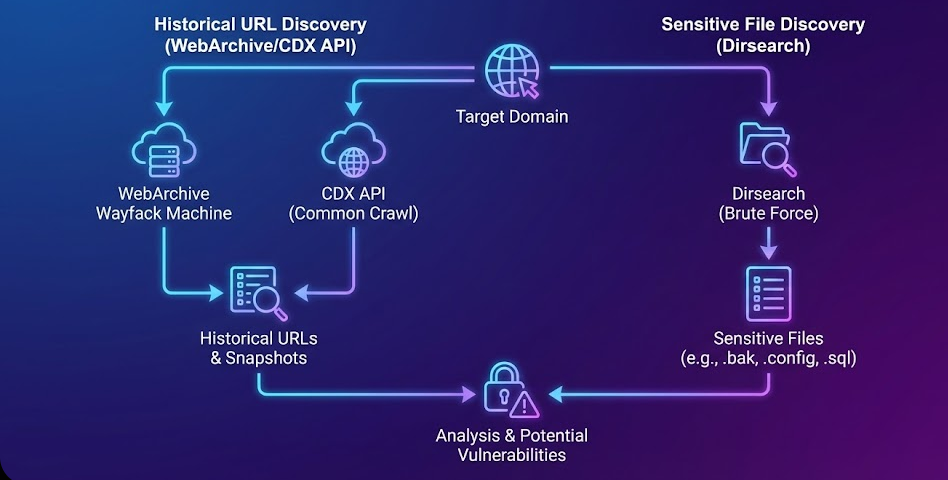
In bug bounty hunting and web application penetration testing, having a strong and well-defined reconnaissance workflow is more important than just running random tools. Most security researchers fail to uncover high-impact vulnerabilities not because they lack skill, but because their recon process is unstructured. A proper recon workflow helps you systematically map the entire attack […]
SOC 2 Audit Failures: The Most Common Reasons Companies Fail — and How to Avoid Them

A SOC 2 audit is a crucial validation for all organisations dealing with customer data. It serves as an indicator that the organisation is applying safe and secure practices. On the other hand, a lot of firms do not pass the SOC 2 compliance audit due to a lack of readiness. The commonly made mistakes are neglecting […]
How to Automate SOC 2 Compliance: Tools, Workflows & Real-Time Gap Detection

SOC 2 compliance has become very important for companies that handle customer data. Many teams struggle because the process is time consuming and requires regular checks. A manual SOC 2 compliance audit often becomes stressful and slow. Such tools are recognized as the most widely used and effective solution nowadays, which is the reason for automation’s successful […]
DNS-Powered Stealth Malware: Unmasking “Detour Dog” and the Rise of TXT-Based Threats

Cybercriminals are no longer just breaking in; they’re learning to blend in. A new, worrying type of malware called “Detour Dog” hides by using parts of the internet that people usually trust. Instead of using obvious methods, it stores and receives information through DNS TXT records — tiny pieces of text that are normally harmless. […]
ISO 27001 vs. SOC 2: Which Compliance Framework Is Right for Your Business?

In the current ever-changing digital environment, cybersecurity and compliance are not optional anymore but a necessity in business. Regardless of whether you work in SaaS, FinTech, or the healthcare industry, it is crucial to make sure that your organization is compliant with global security standards to protect sensitive information and build […]
How to Prepare for a SOC 2 Audit: A Complete Step-by-Step Guide

One of the best methods for organizations to show their dedication to data privacy and security is by achieving SOC 2 compliance. Nevertheless, the process of preparing for a SOC 2 compliance audit can be complicated and may require multiple teams to plan it and document all the necessary information. This guide will take […]
10 Proven Benefits of ISO 27001 Certification for Businesses

In the digital-first world, it is not an option to protect sensitive data anymore but a necessity. The threat of cyberattacks, regulatory scrutiny, and customer expectations regarding data privacy are growing in businesses. Earning ISO 27001 certification proves a business’s dedication to the protection of information assets using a systematic framework that is internationally accepted. […]
7 Key Factors That Can Affect Your ISO 27001 Timeline (And How to Plan Ahead)

Becoming ISO 27001 compliant is one of the key milestones that any organization aiming to enhance its information security posture and gain the trust of its clients must achieve. However, the most common issue that businesses encounter in the process is controlling the timeline of the ISO 27001 certification audit. Some organizations are done in […]

