Content Security Policy (CSP) is a key web security standard that helps defend against a range of content-based attacks, such as Cross-Site Scripting (XSS), Clickjacking, and data injection attacks. By regulating which resources a browser can load and execute, CSP enhances application security by reducing exposure to potentially malicious content.
How Does It Work?
CSP works by allowing site administrators to create a whitelist of trusted sources that browsers can load and render. This list of safe sources is defined using the Content-Security-Policy HTTP header, which specifies what types of resources (like scripts, styles, or images) are allowed on the webpage and where they can originate.
The CSP is typically implemented through HTTP response headers (the preferred and most secure method) or occasionally with HTML <meta> tags, although meta tags have limitations in supporting all CSP directives.
Core CSP Directives
CSP policies consist of multiple “directives” that help control various types of web content. Here are some of the key directives:
- Default Source (default-src): Specifies the default sources for fetching resources like JavaScript, images, fonts, and CSS. If no other directive is set, this rule applies to all resources.
- Script Source (script-src): Defines which sources are trusted for loading JavaScript.
- Style Source (style-src): Controls the sources permitted for loading CSS stylesheets.
- Image Source (img-src): Regulates where images can be loaded from.
Each of these directives acts as a filter, allowing only approved resources to load and helping mitigate unauthorized content injection.
CSP Directive Categories: Controlling Different Aspects of a Web Application
CSP directives are categorized based on their role in regulating different aspects of a web application:
- Fetch Directives: Govern which origins can provide resources like fonts, images, and scripts.
- default-src: Sets fallback sources for fetch requests.
- font-src: Specifies origins for font loading.
- img-src: Defines allowed sources for images.
- script-src: Determines which origins are allowed for script loading.
- Document Directives: Define settings specific to the document’s behavior.
- base-uri: Controls the URLs allowed for the <base> element.
- sandbox: Limits the document’s capabilities, isolating it as if it’s from a separate origin.
- Navigation Directives: Manage where requests can be sent and which origins can embed the page.
- form-action: Restricts where form submissions can be sent.
- frame-ancestors: Defines which origins can embed the page using <iframe> or <object> tags.
- Reporting Directives: Set where CSP violations should be reported.
- report-to: Specifies the endpoint URL for reporting CSP violations.
- Other Directives:
- upgrade-insecure-requests: Automatically upgrades all HTTP requests to HTTPS.
CSP Source Expressions: Fine-Tuning Content Security
CSP source expressions give administrators granular control over which content can load from specific origins. These expressions help enforce security policies more precisely:
- ‘none’: Disables all sources.
- ‘self’: Allows content only from the same origin as the page.
- ‘unsafe-inline’: Permits inline scripts, though using this option is generally discouraged.
- ‘unsafe-eval’: Allows JavaScript functions like eval(), but it’s best avoided due to security risks.
- ‘strict-dynamic’: Allows trusted scripts to load additional scripts dynamically.
With these source expressions, CSP directives become powerful tools to safeguard web applications against risks like XSS by preventing untrusted scripts or media from loading.
CSP Example: The img-src Directive in Action
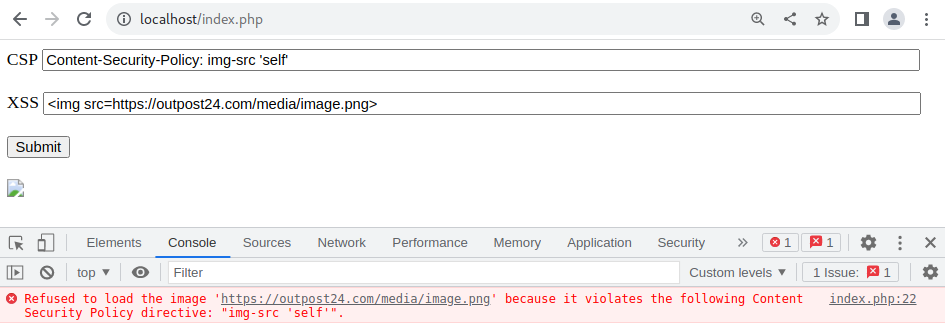
Consider the above scenario where the img-src directive in a CSP policy is set to “self”. This configuration allows images to load only from the same origin as the page—say, localhost. If an attacker attempts to inject an external image to trigger an XSS attack, the CSP policy will block the image from loading. This directive thus ensures that only trusted, internal image sources are rendered, protecting the application from potential XSS vulnerabilities.
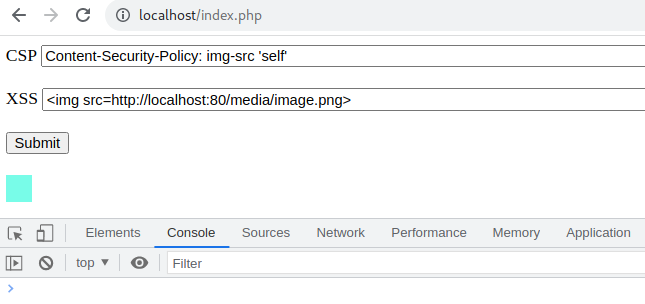
Similarly, if we are using an absolute URL that points to the same resource on the application’s origin rather than a relative path will also allow the image to load without any issues, as shown in the figure below.
CSP Tips for Enhanced Security
- Avoid Wildcards (*): Limit content sources to specific trusted domains rather than using broad wildcards, which open the door to malicious content.
- Disable unsafe-inline and unsafe-eval: Avoid these options whenever possible, as they bypass many of CSP’s security benefits.
- Use HTTPS Only: Always define trusted sources using HTTPS to ensure secure data transfer.
- Regularly Review Policies: As your application evolves, review and update your CSP to adapt to new functionalities and maintain strong security.
Conclusion
By implementing a robust Content Security Policy, web developers can greatly enhance their application’s security, limiting exposure to common injection-based attacks and creating a more secure experience for users.

